In the past few years, the United States has seen an increase in frequency—and an escalation in severity—of attacks on the industrial control systems (ICS) and operation technology (OT) networks that control its critical infrastructure (such as power grids, water systems, communication networks, and transportation systems). In early 2019, a U.S. solar generation company was compromised, causing operators to lose visibility into the system for several hours.
In a 2021 incident, an attacker tried to poison a water supply that serves thousands of Florida residents. The hack of U.S. industrial control networks via SolarWind software to gain sensitive data lasted for at least eight months in 2020–2021. In addition, last year’s “brute force” hacking (i.e., utilizing continuous password attempts) of U.S. electric infrastructure was linked by the National Security Agency to a group from Russia. These incidents, taken together, make clear the need to dramatically ramp up cyber security efforts to defend U.S. critical infrastructure.
In response to the increased incidents and in anticipation of future attacks, the Biden administration in July 2021 issued a national security memorandum outlining the threat, asserting that “the degradation, destruction, or malfunction of systems that control this infrastructure could cause significant harm to the national and economic security of the United States.” U.S. nation-state adversaries—notably China and Russia—are preparing cyber weapons that can attack our military, manipulate the supply chain, and disable our critical infrastructure.
Defending the nation from this advanced threat landscape requires more than the current best practices of patching cyber vulnerabilities and practicing good cyber hygiene. These traditional approaches are effective against lower tier adversaries that can exploit known vulnerabilities to achieve their goals, but they cannot defend systems against highly sophisticated attackers. Experts say, in some cases, it is not feasible to try to keep the more sophisticated adversaries out of U.S. systems and networks. Instead, efforts should focus on making it as costly as possible for them to achieve their objectives and on protecting ICS and OT networks.
As part of the national strategy, LLNL is applying leading-edge science and technology and leveraging its interdisciplinary workforce to directly support these efforts and help inform U.S. policymakers about their impacts. LLNL’s cyber programs work across a broad sponsor space—including the internal Laboratory Directed Research and Development (LDRD) Program—to develop technologies that address the most sophisticated cyber threats directed at disrupting our national security communities and civilian critical infrastructure. Key capabilities in this area include:
- Modeling and simulation of cyber and cyber-physical systems leveraging high performance computing and co-simulation to produce high-fidelity simulations that also capture large-scale impacts
- Advanced data analytics and machine learning to detect and counterinfluence operations in social media and artificial intelligence-driven automated influence campaigns, as well as deep-fake video, audio, and narrative text
- Network mapping, modeling, and analysis capabilities to identify, understand, and characterize behavior on information technology and OT networks
- Automated and scalable software assurance capabilities to protect U.S. supply chains
- Applications for collaborative autonomy and decentralization in control systems
- In-depth analysis to quantify risks to cyber systems from intelligent adversaries and calculate costs/benefits of mitigation strategies
Several Efforts Directed at a Common Goal
At Livermore, computer scientists, software developers and engineers, and cyber experts supporting the Global Security Principal Directorate are working on a suite of projects to secure and fortify U.S. critical infrastructure and networks.
One such project is applying collaborative autonomy to the control of distributed energy resources, such as rooftop solar generation. Collaborative autonomy is a broad term that describes a network of humans and autonomous machine partners interacting and sharing information and tasks. In partnership with the Department of Energy and equipment manufacturers, Livermore staff are incorporating SkyNet into solar inverters.
Currently, rooftop solar generation is controlled by a small number of aggregators that have the capability to send commands to individual inverters (to curtail production when there is an abundance of solar generation, for example). Compromise could allow an adversary to control a broad network of inverters, potentially causing significant disruption to the power grid through malicious commands. SkyNet enables the individual solar inverters to work together to verify and validate commands from central control nodes and reject commands that have the potential to cause damage and disruption.
Another Livermore effort, called Valyrian Steel, seeks to improve the security of software that is used by critical infrastructure by automating the software assurance process. Software assurance is the level of confidence that software is without vulnerability, either intentionally inserted or accidentally added at any point during its lifecycle, and that the software functions in the manner it was intended.
Sponsored by the Department of Homeland Security, Valyrian Steel allows users to create a Software Bill of Materials (SBOM) for device firmware or any other software. Equivalent to the “Nutrition Facts” label on food products, SBOM analyzes software and then relays to a user what software components are present in their critical devices, where those components came from, and identifies code deficiencies and bugs. Being able to perform this analysis in an automated way allows for broad scaling, making it more difficult to compromise supply chains.
A third project in Livermore’s cyber arsenal pairs two technologies—LLNL’s Network Mapping System (NeMS) and the ns3 network simulator—to allow analysts to see our systems through the eyes of adversaries. NeMS is a well-developed and proven software-based tool that provides system owners with a comprehensive view of their computer network environments. It has been shown to consistently identify over 100% of devices on a network. (The accuracy is more than 100% because it finds everything the owner indicates is there along with devices that the owner is unaware of.)
The ns3 open-source, discrete-event network simulator for internet systems can be coupled to NeMS and then applied to a physical process (e.g., the model of power flow in the grid and network that controls the devices on the grid) to create a “digital twin” of the system of interest. The digital twin can then be analyzed with a suite of tools that help identify critical nodes, key failure modes, and potential attack pathways to understand how an adversary might compromise systems. This capability allows analysts to stay ahead of adversaries and prioritize defensive strategies.
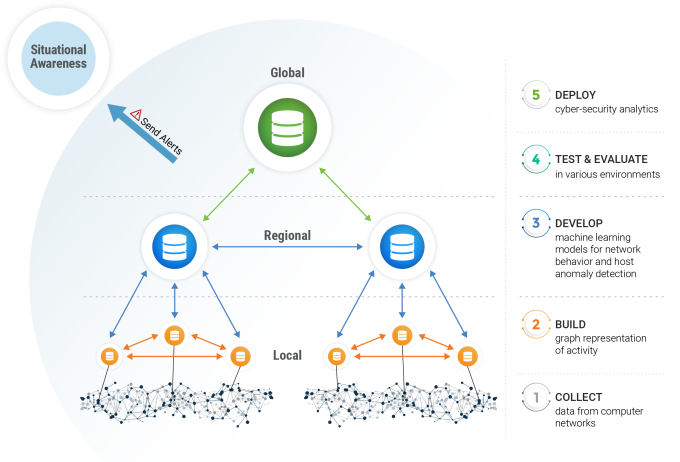
Using Machine Learning to More Effectively Identify Malicious Cyber Behavior
Enterprise antivirus programs have honed the ability to successfully detect and thwart malicious activity on networks and computers through specific, signature-based detection mechanisms. However, further advancements require determining how to model types of malicious behaviors and more general characteristics of cyber threats. This endeavor is still an open area of research, both in industry and government sectors.
“While your traditional cyber defense companies are also looking at this capability, at LLNL we are tailoring our research to government-specific applications that protect critical infrastructure,” says Kristine Monteith, a cyber defense researcher and principal investigator in Global Security’s Information Operations and Assurance Program.
High-fidelity, real-world data can be critical in the development of these types of behavioral models. Using a host-based sensor initially created through SETAC (Supercomputing Enabled Transformational Analytics Capability project), an LDRD Strategic Initiative led by computer scientist Celeste Matarazzo a decade ago, current efforts are bridging the gap by collecting (with permission) behavioral analytic data—that is, sequences of events or running processes on individual LLNL user computers.
“The resulting data set is higher fidelity than would otherwise be available through commercial collection mechanisms,” explains David Frye, a sensor developer and research associate.
“We’re collecting real-world data from users so that we can get statistics on how often various events occur. This work will help us build models to identify anomalous and potentially malicious behavior,” says Grant Johnson, a data engineer and research associate on the project. “The advantage of doing behavioral analytics instead of looking for known malicious files alone is that we will catch things that haven’t been seen before.”
Monteith’s group is using machine learning to train models to identify previously unseen threats. They use labeled data from known malicious events to inform models that can generalize from these known threats to future variants. To expand on what her group is learning, Monteith has participated in several research exchanges over the past few years with investigators working on similar projects. Her team is also in the process of getting approval for the sensor to be released to other government entities. This step will enable an “apples to apples” comparison of data with other parties and allow the machine-learning algorithms to be shared among researchers.
“From a strategic perspective, these models are designed to identify and prevent incidents similar to the SolarWinds attack,” says Monteith. “SolarWinds is a classic example of the type of threat we’re concerned about: bad actors infiltrating our networks in novel ways.”
Staying ahead of the game is essential when it comes to cyber security and resilience. In addition to identifying future emerging technologies that will improve cyber defense, Livermore cyber experts continue to integrate the Lab’s capabilities with intelligence analysis to make them more relevant and impactful for U.S. policymakers, the intelligence community, and the military.